These articles and blog posts are my own opinion and do not reflect the view of my employer.
Sorry to keep everyone waiting! Here in this series, I will be inspecting anti-virus vendors,
taking a deep dive on detection. Using common tools that you may use to bypass AV.
A quick run down of the test scenario is as follows:
* Simulate phishing/watering hole attack by hosting executable on Linux Server
* Download the executable. What happens? Does the AV report anything, log, or block?
* Click the executable. Same as before. Report, log, block?
* If the AV does not block then a session is gained on the attacker’s machine. The attacker will attempt a privilege escalation and/or persistence.When doing these actions does the AV report, log, or block?
* After successful privilege escalation perform a hashdump, UID check, and privilege check.
Instead of looking at completely bypassing AV, a part I will be looking at is detection. Working with defense in depth is key and I will explore why that is important. If your anti-virus is bypassed, instead of accepting the fact, what can be done about it? The second part will take a dive into basic forensics and tools. Where signs of compromise can be seen, so that in the unfortunate event that this happens you can be prepared on artifacts to expect. Full disclosure, this will not follow a sound forensics step by step (while that can be included in the improvements), but rather to show popular tools and get an idea to deal with compromise. We don’t want our security products to open the door for malware and attackers, but see how they are checking stuff at the door. Potentially leaving us key clues to how everything happened.
I will also break down the vendors into two different categories. For home and business use. While the home editions, I don’t expect to have a forensics case underway, this might help family and friends understand when something is not right.
As the tests continue, each attack will increase in sophistication. The reality is the more sophisticated the attack, the less detection you will receive. This is not a series of posts to bash AV. I want to bring awareness that these tools are easy to get ahold of. Even with the VMs fully updated and patched.
Now on to the good stuff.
This week we will be looking at AVG Internet Security Business Edition. The executable can be located here: http://www.avg.com/us-en/business-security
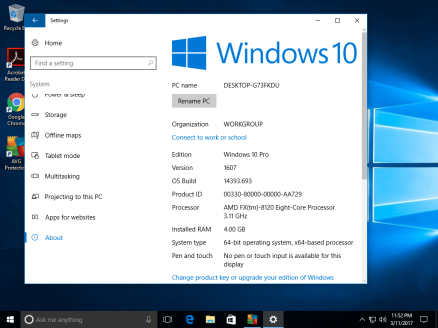
The VM where the testing happens is a Windows 10 Pro with all updates installed. I have also installed “business applications” such as: Microsoft Office 2013, Adobe Reader, 7zip, and Google Chrome. These can be found on this page here: https://virtualizedcomputing.wordpress.com/applications-used-windows/


The VM has a 4GB RAM, 2 cores, and a 30GB drive. This gives it moderate speed when doing testing.
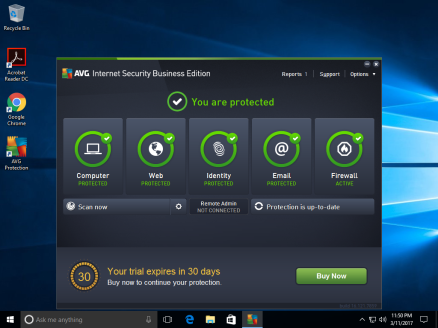
For AVG, I have installed default settings and have turned on default settings. The application is up to date and have the initial scan already complete.
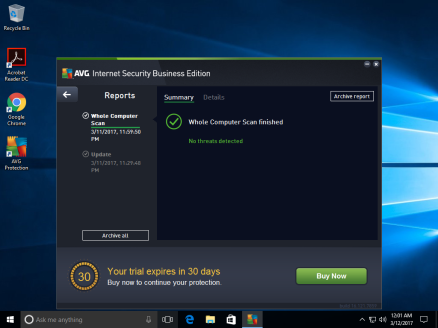
Also to show that Windows Defender is not running:

On the attacker VM, I have chosen Kali Linux. This is fully updated as well. Applications that are installed beyond the default configuration can be found here: https://virtualizedcomputing.wordpress.com/application-used-linux/
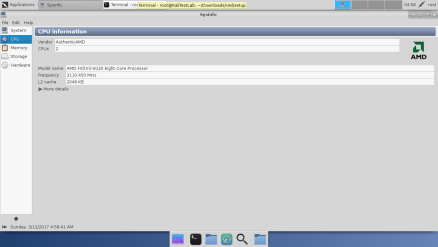
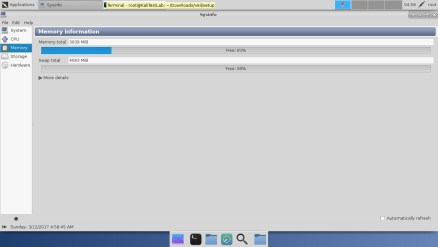
Kali Linux VM has 4GB RAM, 2 cores, and 25GB drive.
All default were accepted for Veil-Framework, Shellter, and Metasploit Framework (created the DB).
This will end Part 1 for configuring the environment for the test. Next I will show how to launch payloads and evade AV! How hard do you think it will be to bypass?
If you have any comments, critiques, or improvments please feel free to comment below. You can also connect with me on Twitter at https://twitter.com/_TacoRocket
Awesome sauce, looking forward to the series!
LikeLike
Thank you!
LikeLike
[…] Continuing from the previous blog post here: https://virtualizedcomputing.wordpress.com/2017/03/12/av-evasion-tools-to-bypass-av-avg-internet-sec… […]
LikeLike
[…] https://virtualizedcomputing.wordpress.com/2017/03/12/av-evasion-tools-to-bypass-av-avg-internet-sec… […]
LikeLike
[…] Part 1 can be found here. […]
LikeLike